An Introduction to Message Bus Technology in Networking
In today’s interconnected digital world, ensuring seamless communication between various applications and services is crucial. This is where the Message Bus Architecture comes into play.
What is a Message Bus?
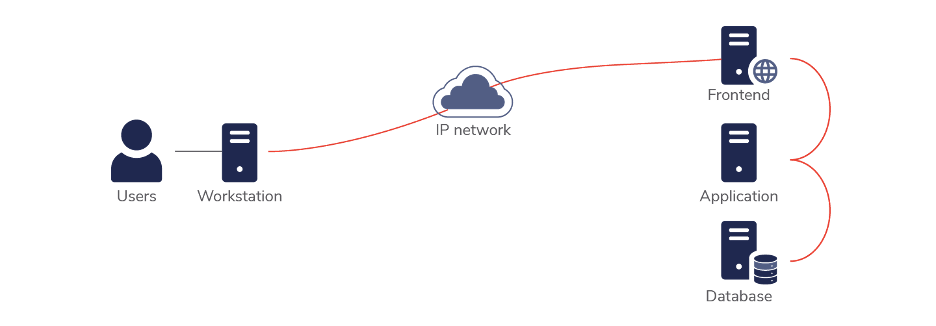
A Message Bus, or Enterprise Service Bus is a communication system enabling seamless data exchange between network components.
Imagine a bustling city with numerous neighborhoods, each representing a different application or service. To keep the city running smoothly, these neighborhoods need to exchange information efficiently. A Message Bus acts like the city’s central transit system, ensuring messages (data) are delivered to the right destinations without any direct connections between them.
In technical terms, a Message Bus is a system that enables different applications, services, or systems to communicate by transmitting messages through a shared infrastructure. This setup ensures that each component remains independent, promoting flexibility and scalability.
Key Components of Message Bus Architecture
1. Producers (Pollers)
In the opHA Message Bus system, pollers act as producers. They collect data from various network devices and systems, generating messages that contain critical information about network performance, events, and statuses. These pollers can be scaled horizontally or vertically, ensuring efficient data collection across expansive networks.
2. Broker (opHA Message Bus)
Serving as the central communication hub, the opHA Message Bus ensures real-time synchronization among multiple pollers. It manages the routing of messages from producers to consumers, maintaining data integrity through message replication across three nodes, which allows the system to tolerate single-node failures.
3. Consumers (Primary Server and Applications)
The primary server and associated applications like opCharts and opEvents function as consumers. They receive and process messages relayed by the Message Bus, providing users with a consolidated, real-time view of network health and performance. This setup enhances capabilities such as event logging, monitoring, and the generation of intuitive dashboards and reports.
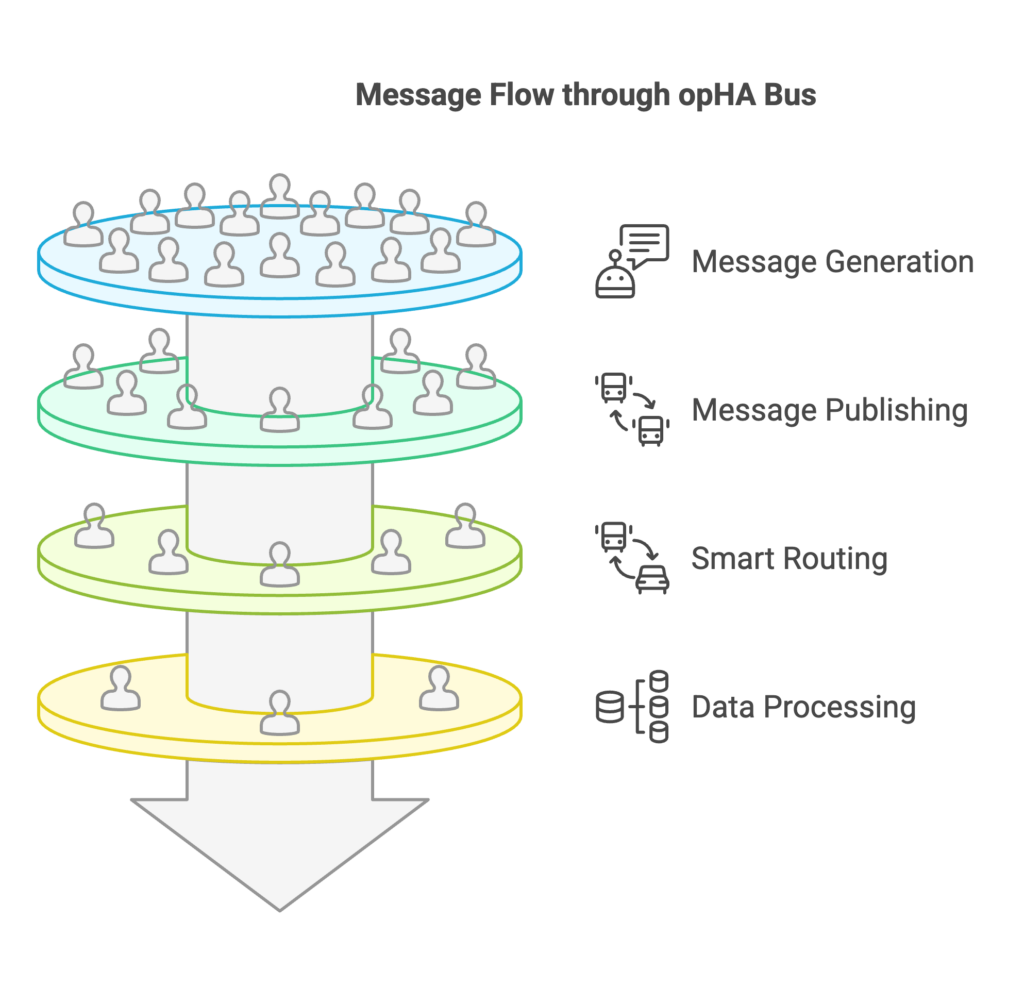
How Messages Flow Through the opHA Message Bus
- Generating Messages: Pollers (producers) collect data from network devices and generate messages containing key information.
- Publishing to the Bus: These messages are sent to the opHA Message Bus, which acts as the central broker.
- Smart Routing: The Message Bus identifies which applications or services (consumers) need the data and directs messages accordingly.
- Processing & Action: Consumers, such as the primary server, opCharts, and opEvents, receive the messages, process the data, and trigger the necessary actions, such as alerts or dashboard updates.
By keeping producers and consumers decoupled, this architecture allows each component to function independently. This improves flexibility, scalability, and resilience—ensuring efficient network management even as demands grow. 🚀
Common Use Cases for Message Bus Technology
1. Microservices Architecture
In modern network management and cybersecurity environments, different services handle distinct functions—such as network monitoring, security alerts, performance analytics, and automation workflows—while seamlessly communicating with each other. The opHA Message Bus acts as the backbone for this communication, ensuring that services remain loosely coupled, scalable, and resilient in distributed architectures.
✅ Benefits in Network Management Microservices:
- Seamless Data Flow: Ensures real-time data exchange between network monitoring tools, security systems, and reporting dashboards.
- Scalability: Allows IT teams and MSPs to add or modify monitoring components without affecting the entire system.
- Reduced Latency & Bottlenecks: Distributes network event data efficiently, preventing system slowdowns.
- Asynchronous Processing: Enables automated alerts, log analysis, and device polling without delays.
2. Event-Driven Systems
Modern applications rely on real-time event processing to improve responsiveness and automation. A Message Bus is a core component of event-driven architectures, where events (e.g., user actions, system changes, external triggers) are published and consumed dynamically.
✅ Where It’s Useful:
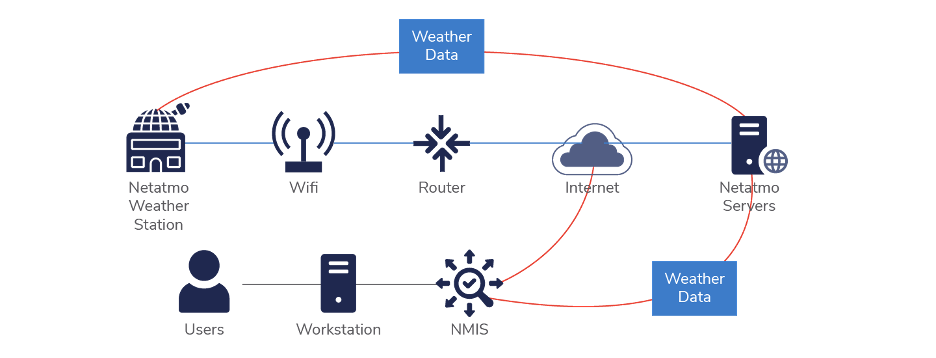
- IoT Networks: Devices publish sensor data, and analytics engines process it instantly.
- Cybersecurity Monitoring: Suspicious activity is flagged and sent to security systems in real time.
- Finance & Banking: Fraud detection systems react instantly to unusual transactions.
Benefits of Message Bus Technology for MSPs
4. Multi-Tenancy Support
For Managed Service Providers (MSPs), managing multiple clients efficiently is critical. The opHA Message Bus is designed for multi-tenancy, allowing MSPs to handle multiple customer environments within a single infrastructure.
✅ Why Multi-Tenancy Matters:
- Centralized control over multiple client networks.
- Resource efficiency by sharing infrastructure while keeping data isolated.
- Easy configuration for different clients, reducing operational complexity.
- Security & Compliance ensure customers only access their designated data.
5. Fault Tolerance and High Availability
To ensure uninterrupted operations, the opHA Message Bus is built with fault tolerance and redundancy mechanisms that keep services running even if individual components fail.
✅ How It Enhances Network Reliability:
- Message replication across multiple nodes prevents data loss.
- Automatic failover ensures continued service if a broker or poller fails.
- Load balancing distributes workload efficiently, avoiding bottlenecks.
- Self-healing mechanisms can re-route traffic dynamically to maintain uptime.
Final Thoughts
The opHA Message Bus is a powerful tool for MSPs and enterprises managing complex network environments. Its ability to support microservices, real-time event processing, and high-throughput data streaming makes it a cornerstone for modern IT architectures.
Would you like to learn more about how the opHA Message Bus can enhance your network management strategy? Explore more here. 🚀