IT Process Automation (ITPA), also known as process automation, is a strategic approach that leverages software tools to automate repetitive tasks, streamline business processes, and enhance the efficiency of IT operations. It is a key component in the digital transformation journey of many organizations, enabling them to achieve positive business outcomes by automating routine tasks and creating consistent process frameworks with a process automation solution.
IT Process Automation Definition
IT Process Automation (ITPA) is a method of using software tools to automate and streamline repetitive and routine IT tasks, thereby improving efficiency and reducing the risk of human error.
Understanding IT Processes
An IT process refers to a standardized workflow that helps streamline all information technology-related activities within a company. These processes, which include ticketing system management, asset management, and service requests handling, form the backbone of an organization’s IT infrastructure. They ensure the efficient delivery of services and minimize error potential in everyday IT-related activities.
When Would an Organization Use Process Automation?
Organizations turn to process automation in a variety of scenarios, all aimed at improving efficiency, reducing errors, and freeing up staff for more strategic tasks. The following are examples of when an organization could use a process automation solution.
1. Repetitive Tasks
If an organization has tasks that are repetitive and time-consuming, such as data entry, form filling, ticketing system or report generation, process automation can be used to perform these tasks more efficiently and accurately. This not only saves time but also reduces the risk of human error.
2. Streamlining Processes
When an organization wants to streamline its business processes, it typically employs process automation. This workflow automation could be anything from automating the employee onboarding process to streamlining the handling of service requests. By automating these processes, organizations can ensure consistency and efficiency.
3. Reducing Costs
Process automation can lead to significant cost savings. By using process workflows to automate routine tasks, organizations can reduce the need for manual labor, leading to lower operational costs.
4. Improving Customer Service
Process automation can also be used to improve customer service. For example, automation can be used to handle customer inquiries, process orders, and provide timely responses. This can lead to improved customer satisfaction and loyalty.
5. Risk Management and Compliance
Organizations in regulated industries often use process and automation technologies to ensure compliance with regulations. Automated processes can be designed to follow specific rules and standards, reducing the risk of non-compliance.
6. Data Analysis and Decision-Making
Process automation tools often come with analytics capabilities that can provide valuable insights into business operations. These insights can be used in change management helping the business to make better-informed decisions resulting in improved business outcomes.
Process automation is a versatile tool that can be used in a variety of scenarios to improve efficiency, reduce costs, and enhance customer service. By identifying tasks that are suitable for automation, organizations can make the most of this technology and reap its many benefits.
Types of Process Automation
Process automation comes in various forms, each designed to address specific needs within an organization.
Robotic Process Automation (RPA)
Robotic Process Automation (RPA) is a type of process automation technology that uses bots to perform high-volume, repetitive tasks such as data entry. It promotes cost savings and greater efficiency in processes that involve extensive documentation.
Business Process Automation (BPA)
Business Process Automation (BPA), on the other hand, is a broader concept that focuses on automating complex business operations to streamline and reduce costs. It is often associated with digital transformation initiatives aimed at improving customer satisfaction and operational efficiency.
IT Process Automation (ITPA)
ITPA, a specialized form of process automation, focuses on automating IT tasks. It uses process automation software to automate complex business operations and often time-consuming tasks, reducing the need for human intervention and improving efficiency.
How Does IT Process Automation Work?
ITPA operates on an action-reaction system. It uses automation software to monitor business applications and track system performance metrics. When a predefined event occurs, the ITPA system detects it and kick-starts an automated workflow. This reaction can be anything from steps to restore system performance, directing workflows to the service desk, or automated spreadsheet operations. This is how process automation works to streamline IT processes and reduce the burden on the whole IT department or team.
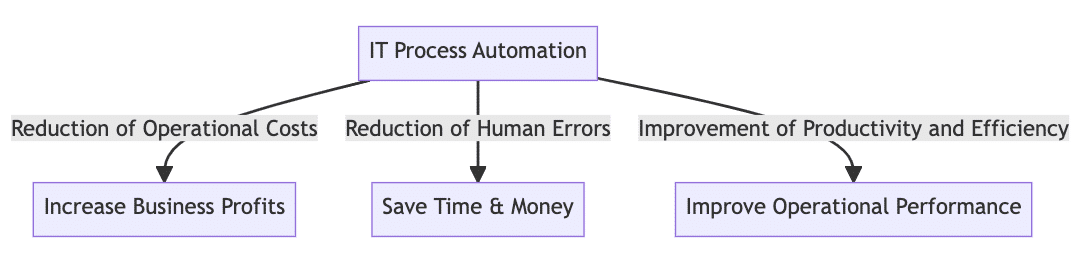
Benefits of IT Process Automation
One of the primary benefits of ITPA is the reduction of operational costs. By automating routine tasks, businesses can streamline IT management without having to increase headcount. This leads to cost savings and allows the IT department to focus on more strategic tasks.
ITPA also reduces the scope of human errors in business systems, minimizing the risk of system malfunctions and security events. By automating IT processes, businesses can ensure a more consistent and standardized approach to handling service requests and managing IT infrastructure.
Furthermore, ITPA improves productivity and efficiency by offloading routine tasks from the IT team. It also enables quicker detection and response rates, improving service levels and enhancing the overall user experience.
Challenges and Limitations of IT Process Automation
Despite its numerous tangible benefits, ITPA also has its challenges. One of the main concerns is the potential for job loss as automation replaces manual tasks. This can lead to a reduction in the number of IT staff needed to perform certain tasks.
Another challenge is the potential for complacency among IT teams. Knowing that most of the routine tasks will be taken care of automatically can lead to a lack of vigilance in monitoring and maintaining IT systems.
Furthermore, the implementation of ITPA can lead to a loss of the human element in decision-making. While automation can handle routine tasks efficiently, there are instances where human intuition and decision-making skills are invaluable.
IT Process Automation Software
ITPA software applications and process automation tools help streamline IT operations by automating and eliminating repetitive work, manual workflows, tasks, and processes. These tools can be implemented across multiple databases and systems and can help automate processes between them without the need for human intervention.
Based on predefined control workflows, your ITPA tool can automatically identify tasks to remediate a system issue or send alerts or escalations to the appropriate IT team members. Some examples of ITPA tools include the automation capabilities within FirstWave’s network management suite of products and Robotic Process Automation (RPA) products.
IT Process Automation Use Cases
IT Process Automation (ITPA) can be applied in various IT processes, offering significant benefits in terms of efficiency, accuracy, and cost savings. Here are some expanded use cases, including examples and case studies from FirstWave:
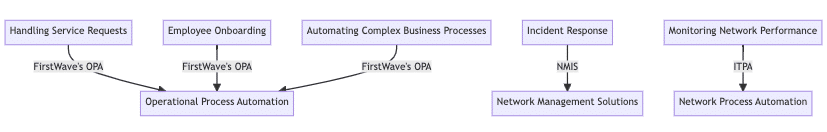
- Handling Service Requests: One of the most common applications of ITPA is the automation of service requests. For instance, when a service request is received, the ITPA tool can automatically categorize and prioritize the request, assign it to the appropriate IT team member, and even provide automated responses to common issues. This not only speeds up the response time but also ensures consistency and reduces the risk of errors. The automation capabilities within FirstWave’s network management suite of products are designed to streamline this process, offering an intuitive user interface and automated workflows to handle service requests efficiently.
- Employee Onboarding: ITPA can significantly streamline the employee onboarding process. It can automate the process of setting up new user accounts, provisioning resources, and providing access to necessary systems and applications. This not only speeds up the onboarding process but also ensures consistency and reduces the risk of errors. The automation capabilities within FirstWave’s network management suite of products can be used to automate these tasks, ensuring a smooth and efficient onboarding process for new employees.
- Incident Response: ITPA can be used to improve incident response times. By integrating ITPA with network management solutions like NMIS, organizations can automate the process of detecting and responding to incidents. This can lead to faster response times, reduced downtime, and improved operational efficiency. Our blog post on “Streamlining Incident Response” provides a detailed case study on how ITPA can be used to enhance incident response.
- Network Process Automation: ITPA can be used to automate various network processes, allowing IT teams to focus on more strategic tasks. For instance, it can be used to automate the process of monitoring network performance, detecting anomalies, and initiating corrective actions. Our blog post on “Network Process Automation: Focus on Tasks” provides insights into how ITPA can be used to automate network processes.
- Automate Complex Business Processes: ITPA can also be used to automate complex business operations that involve multiple steps and require coordination between different systems and applications. For instance, it can be used to automate the process of managing change requests, ensuring that all steps are followed correctly and that all necessary approvals are obtained. The automation capabilities within FirstWave’s network management suite of products offer the capability to automate these complex processes, ensuring accuracy and efficiency.
ITPA offers a wide range of applications, from automating routine tasks to streamlining business processes. By leveraging ITPA, organizations can improve efficiency, reduce errors, and free up their IT teams to focus on more strategic tasks.
The Future of IT Process Automation
The future of ITPA is promising, with new technologies such as AI and machine learning expected to play a significant role in its evolution. These technologies can help automate more complex tasks and provide more intelligent and adaptive automation solutions for business users.
For instance, AI can be used to analyze patterns and trends in IT processes, enabling automation software to make more informed decisions and predictions. Machine learning, on the other hand, can enable the software to learn from past experiences and improve its performance over time.
Conclusion
To sum up, IT Process Automation serves as a potent tool aiding businesses in streamlining their IT processes, enhancing efficiency, and cutting costs. By automating routine tasks, businesses can free up their IT teams to focus on more strategic tasks and improve the overall efficiency of their operations.
However, it’s important to remember that automation is not a silver bullet. It’s a tool that can help improve efficiency, but it’s not a replacement for a well-trained, well-equipped IT team. The human element is still crucial in IT operations, and automation should be used as a tool to augment, not replace human skills and expertise.
As businesses continue to evolve and adopt new technologies, the role of IT Process Automation will only become more important. By understanding what is IT Process Automation and how it can benefit your business, you can make informed decisions about how to best leverage this technology to improve your operations and achieve your business goals.